WeActis empowers your employees to take easy actions to secure your at-risk data in Microsoft 365 before AI exposes it, ensuring continuous risk reduction.

IN A NUTSHELL
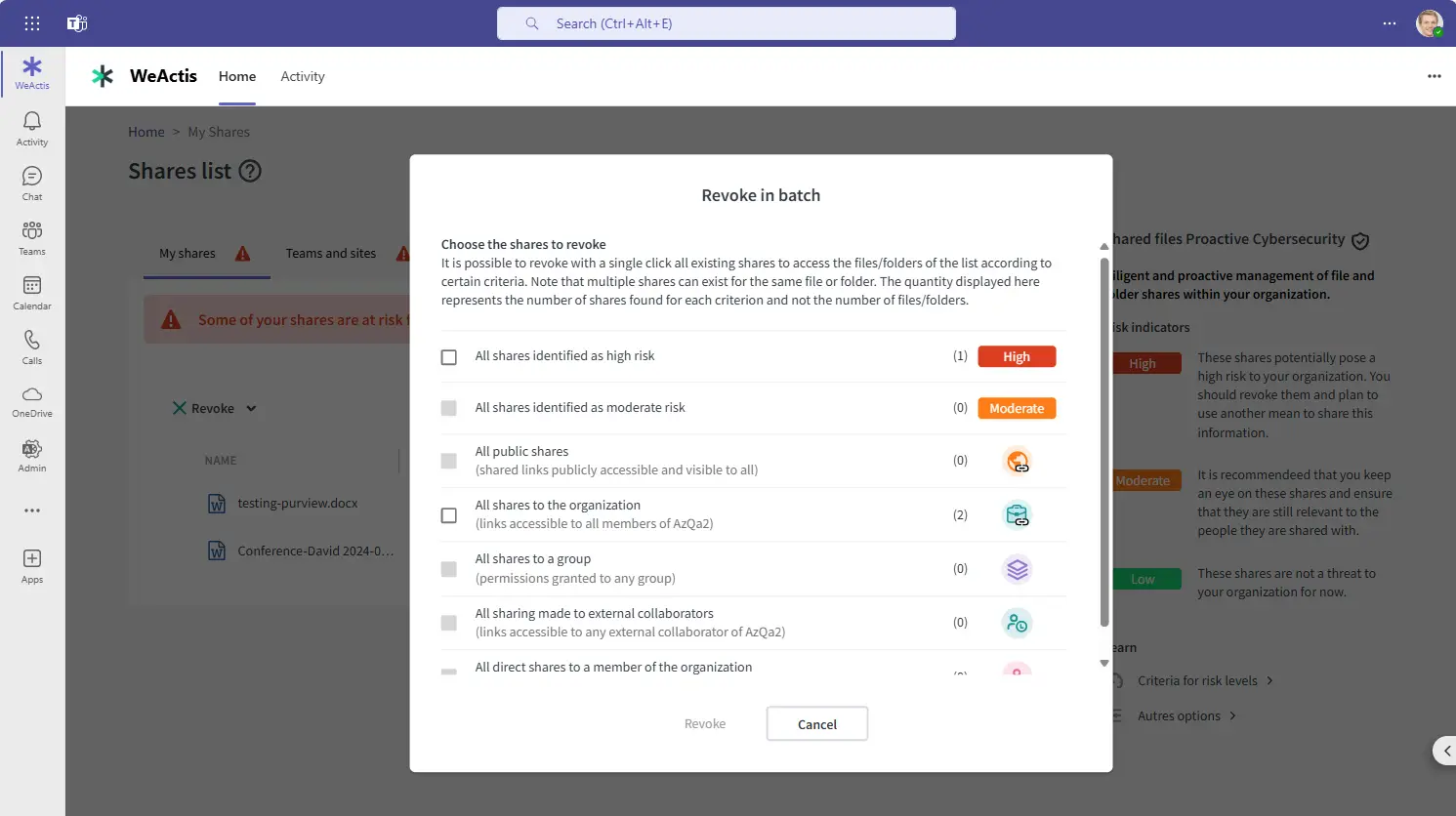
WeActis is a Microsoft Teams-integrated assistant that guides employees in adopting safe behaviors to reduce the risk of data overexposure in less than two minutes per week.
PROBLEM
In today’s digital workplace, platforms such as Microsoft 365 Teams, OneDrive, and SharePoint serve as the backbone of collaboration. Employees generate and share vast amounts of unstructured and sensitive data daily, often without being aware of the risks involved. This creates a perfect storm for data leakage, cyberattacks, and compliance violations.
Years of oversharing and unmanaged data in Microsoft 365 can increase the risk of leaks, non-compliance, and cyberattacks.
90% of the organizations have sensitive files exposed to all employees in M365
– Varonis 2025
Mountains of unsecured Microsoft 365 data hinder security efforts because IT teams lack business context.
69% of employees intentionally bypassed cybersecurity guidance in the last 12 months
– Gartner 2024
Traditional training informs but doesn’t equip employees with the confidence and tools to make secure, measurable decisions.
Business pressure to scale Microsoft 365 Copilot isn’t going away, and AI makes hidden data exposures more visible, searchable, and impactful, turning yesterday’s tolerated risk into today’s business priority.
Without ongoing data hygiene, sensitive info can surface via AI tools before IT recognizes it as at risk.
SOLUTION
The quickest way to lower data exposure risks is to know what data you have, where it’s stored, and how it’s shared, before AI or attackers find it.
WeActis enables you to:

Organizations that lock down Microsoft 365 functionality too heavily undermine the employee experience and struggle with user adoption. Many of these users turn to shadow IT to get their work done, which increases risk.
Gartner 2023

WeActis transforms employees into active risk reducers by fostering secure actions through a positive, effortless, and innovative approach.
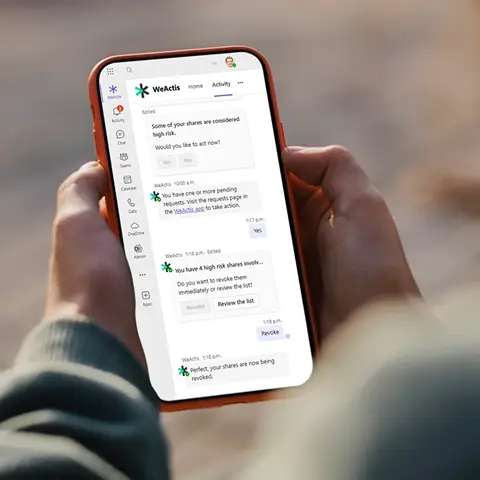
A Microsoft Teams-integrated assistant that makes risk reduction part of daily work.
Contextual, actionable guidance for quick, secure data hygiene actions.
Visibility and gamification to reward lasting safe behaviors that lower risk.
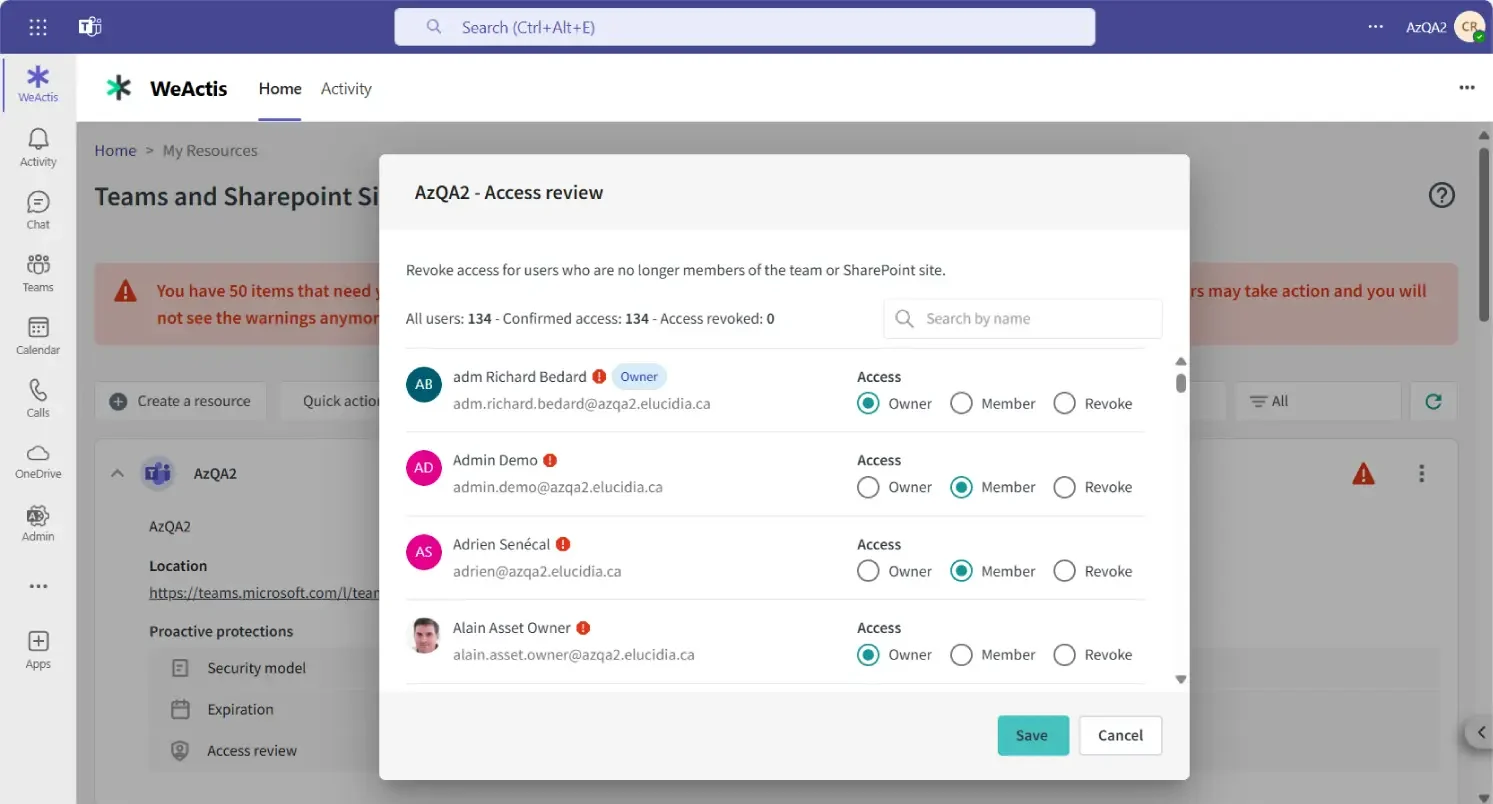
USER EXPERIENCE:
“At the end of a project, I never used to revoke access for collaborators. Now, with WeActis, it’s part of my project cycle.”

Project Manager
IT & SECURITY EXPERIENCE:
“I was facing an impossible problem: if I revoked access, I disrupted business processes, but if I didn’t, I risked compromising business security. WeActis enables a Win-Win situation.”

IT Administrator
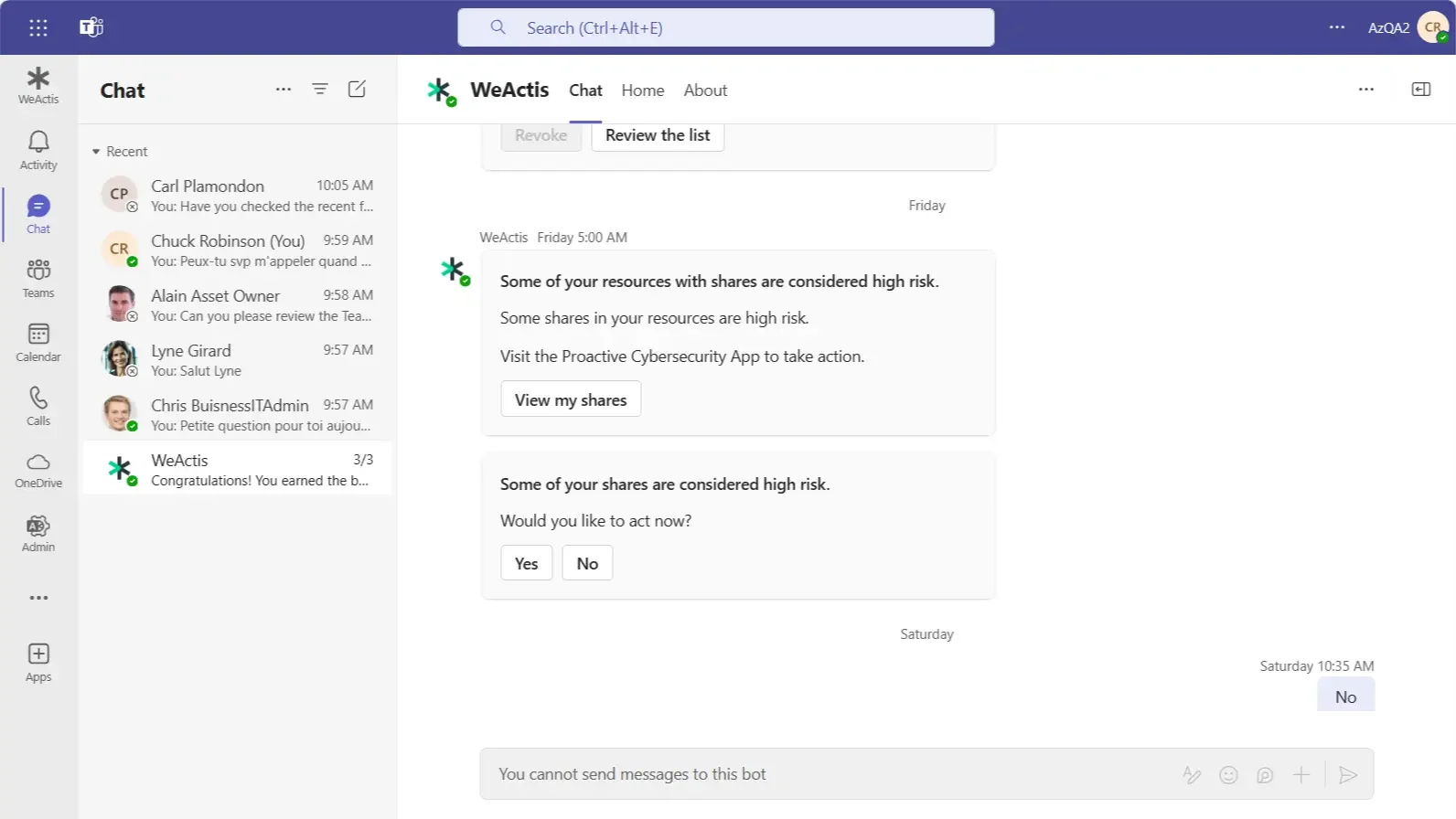
USER EXPERIENCE:
“I don’t have time to choose the expiration date or read-only access when sharing files. WeActis flags these security risks so I can address them quickly.”

Marketing Coordinator
IT & SECURITY EXPERIENCE:
“We can easily set up strict sharing settings for users, but this will limit their work and result in shadow IT. WeActis educates employees while sharing the responsibility.”

CISO
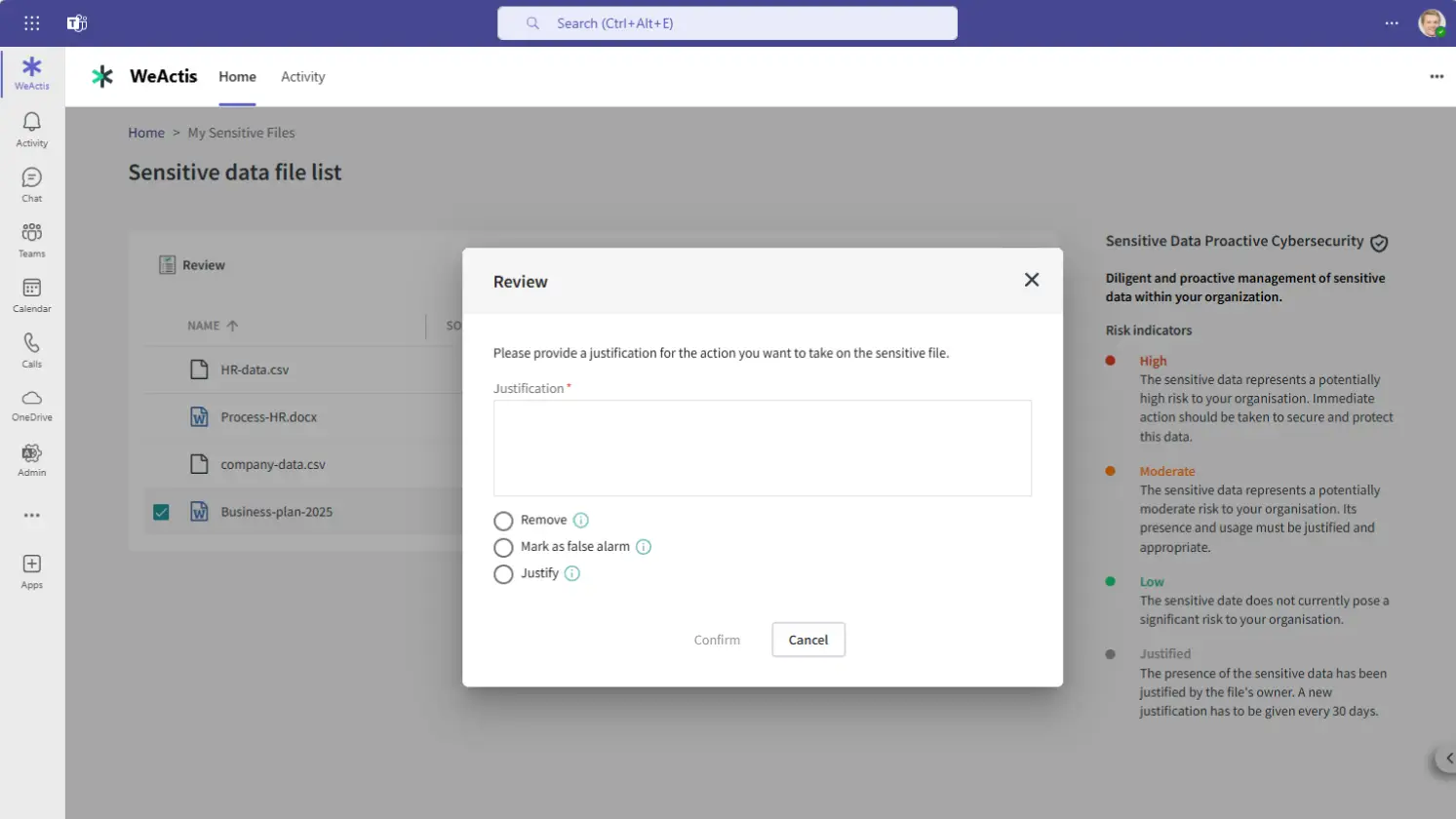
USER EXPERIENCE:
“I was surprised to find credit card data on my workstation. Thankfully, I was able to remove the sensitive files quickly.”

Financial Controller
IT & SECURITY EXPERIENCE:
“With Purview, I received many data security alerts, but they were not actionable for me without context. Now, employees themselves can mitigate risks.”

Security Specialist
USER EXPERIENCE:
“I frequently share files but didn’t realize it could increase my organization’s cyber-attack and compliance risks. With WeActis, I can help in just a few clicks.“

Operations Manager
IT & SECURITY EXPERIENCE:
“When we first used WeActis, we realized that 90% of the links were obsolete. Fortunately, I could revoke the riskiest ones with just a few seconds!“

IT Director
Download WeActis from
Microsoft App store
BENEFITS
By addressing the root of collaboration risks, WeActis empowers employees to develop secure habits that continuously reduce data exposure.


Learn how WeActis works, protects your data, and integrates seamlessly into your organization.
We will reach out shortly to better understand your needs and customize your demo.
Looking forward to connecting soon!
— The WeActis Team
